Cybersecurity researchers have revealed a new attack method targeting AI browsers, which they refer to as AI sidebar spoofing. This attack exploits users’ growing habit of blindly trusting instructions they get from artificial intelligence. The researchers successfully implemented AI sidebar spoofing against two popular AI browsers: Comet by Perplexity and Atlas by OpenAI.
Initially, the researchers used Comet for their experiments, but later confirmed that the attack was viable in the Atlas browser as well. This post uses Comet as an example when explaining the mechanics of AI sidebar spoofing, but we urge the reader to remember that everything stated below also applies to Atlas.
How do AI browsers work?
To begin, let’s wrap our heads around AI browsers. The idea of artificial intelligence replacing, or at least transforming the familiar process of searching the internet began to generate buzz between 2023 and 2024. The same period saw the first-ever attempts to integrate AI into online searches.
Initially, these were supplementary features within conventional browsers — such as Microsoft Edge Copilot and Brave Leo — implemented as AI sidebars. They added built-in assistants to the browser interface for summarizing pages, answering questions, and navigating sites. By 2025, the evolution of this concept ushered in Comet from Perplexity AI — the first browser designed for user-AI interaction from the ground up.
This made artificial intelligence the centerpiece of Comet’s user interface, rather than just an add-on. It unified search, analysis, and work automation into a seamless experience. Shortly thereafter, in October 2025, OpenAI introduced its own AI browser, Atlas, which was built around the same concept.
Comet’s primary interface element is the input bar in the center of the screen, through which the user interacts with the AI. It’s the same with Atlas.
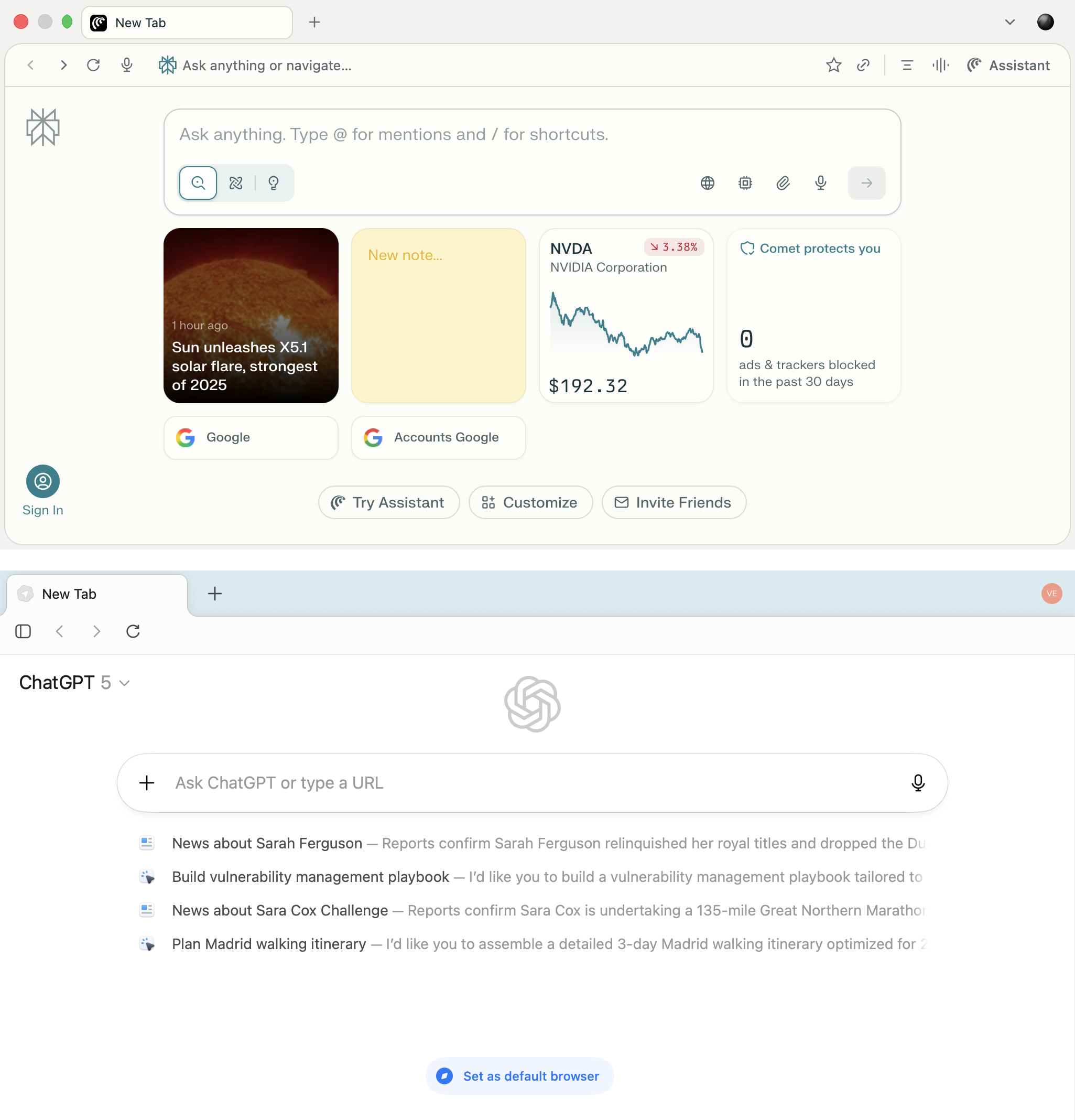
The home screens of Comet and Atlas demonstrate a similar concept: a minimalist interface with a central input bar and built-in AI that becomes the primary method of interacting with the web
Besides, AI browsers allow users to engage with the artificial intelligence right on the web page. They do this through a built-in sidebar that analyzes content and handles queries — all without having the user leave the page. The user can ask the AI to summarize an article, explain a term, compare data, or generate a command while remaining on the current page.
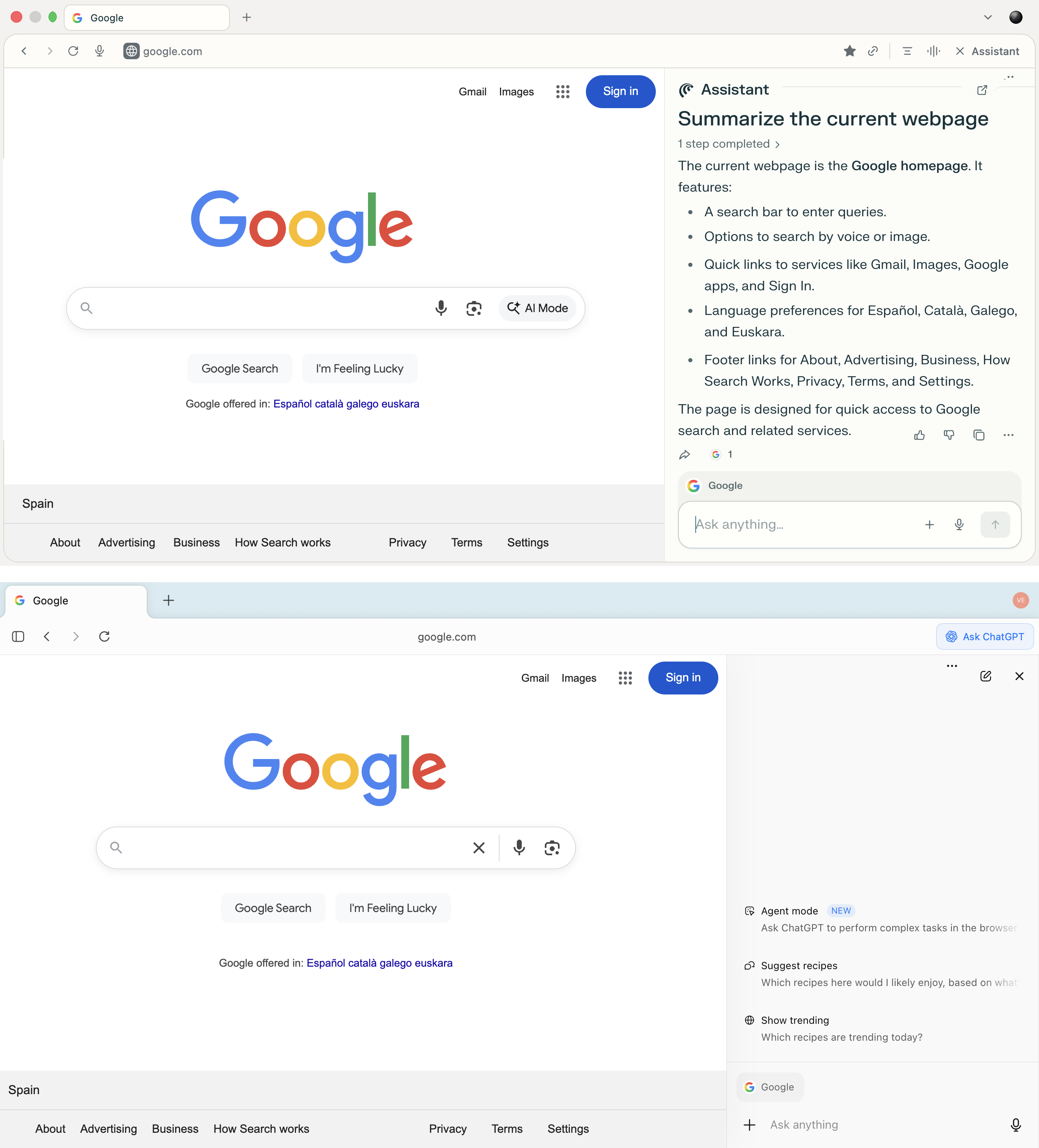
The sidebars in both Comet and Atlas allow users to query the AI without navigating to separate tabs — you can analyze the current site, and ask questions and receive answers within the context of the page you’re on
This level of integration conditions users to take the answers and instructions provided by the built-in AI for granted. When an assistant is seamlessly built into the user interface and feels like a natural part of the system, most people rarely stop to double-check the actions it suggests.
This trust is precisely what the attack demonstrated by the researchers exploits. A fake AI sidebar can issue false instructions — directing the user to execute malicious commands or visit phishing websites.
How did the researchers manage to execute the AI sidebar spoofing attack?
The attack starts with the user installing a malicious extension. To do its evil deeds, it needs permissions to view and modify data on all visited sites, as well as access to the client-side data storage API.
All of these are quite standard permissions; without the first one — no browser extension will work at all. Therefore, the chances that the user will get suspicious when a new extension requests these permissions are almost zero. You can read more about browser extensions and the permissions they request in our post Browser extensions: more dangerous than you think.
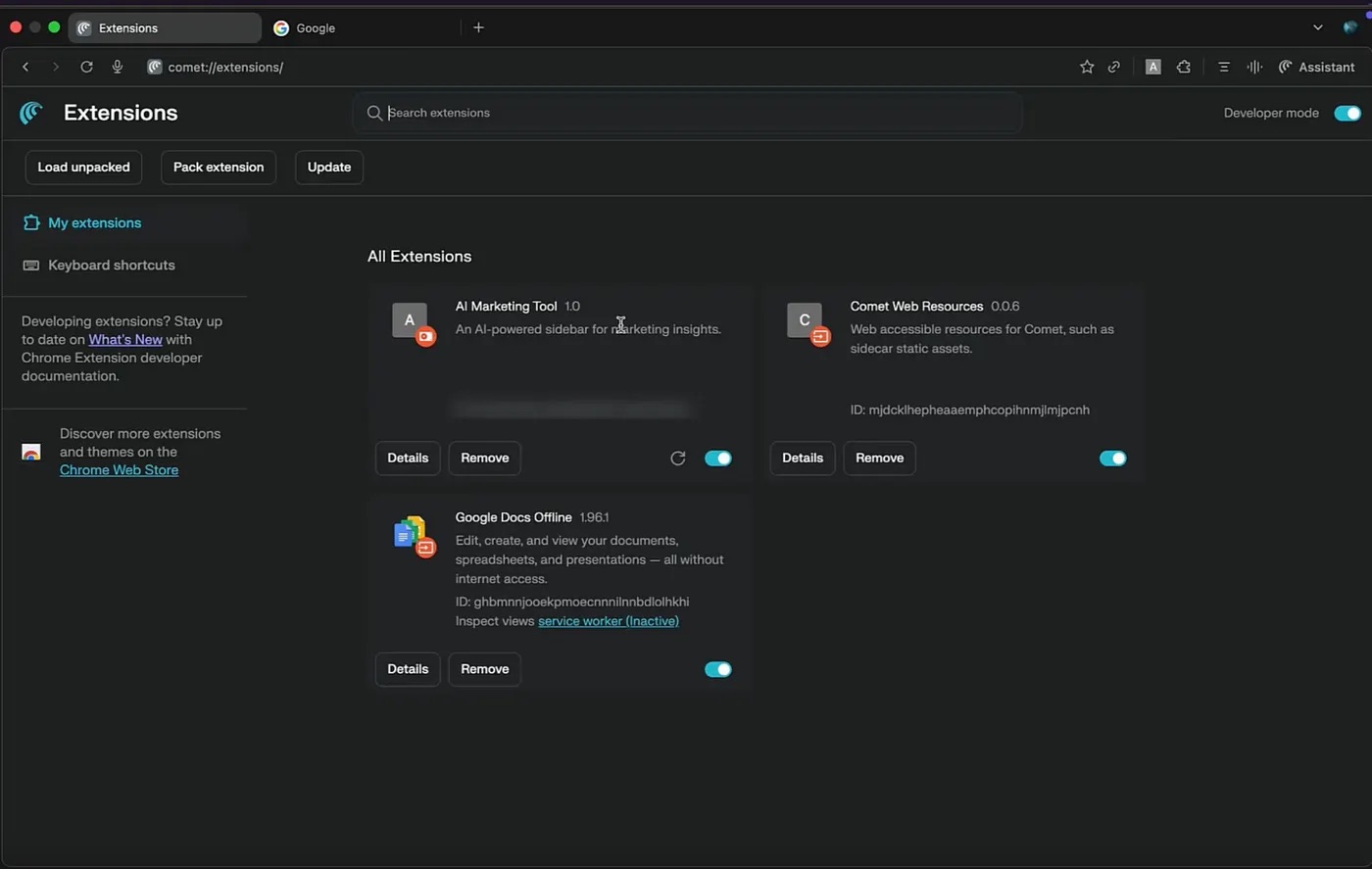
A list of installed extensions in the Comet user interface. The disguised malicious extension, AI Marketing Tool, is visible among them. Source
Once installed, the extension injects JavaScript into the web page and creates a counterfeit sidebar that looks strikingly similar to the real thing. This shouldn’t raise any red flags with the user: when the extension receives a query, it talks to the legitimate LLM and faithfully displays its response. The researchers used Google Gemini in their experiments, though OpenAI’s ChatGPT likely would have worked just as well.
The screenshot shows an example of a fake sidebar that’s visually very similar to the original Comet Assistant. Source
The fake sidebar can selectively manipulate responses to specific topics or key queries set in advance by the potential attacker. This means that in most cases, the extension will simply display legitimate AI responses, but in certain situations it will display malicious instructions, links, or commands instead.
How realistic is the scenario where an unsuspecting user installs a malicious extension capable of the actions described above? Experience shows it is highly probable. On our blog, we’ve repeatedly reported on dozens of malicious and suspicious extensions that successfully make it into the official Chrome Web Store. This continues to occur despite all the security checks conducted by the store and the vast resources at Google’s disposal. Read more about how malicious extensions end up in official stores in our post 57 shady Chrome extensions clock up six million installs.
Consequences of AI sidebar spoofing
Now let’s discuss what attackers can use a fake sidebar for. As noted by the researchers, the AI sidebar spoofing attack offers potential malicious actors ample opportunities to cause harm. To demonstrate this, the researchers described three possible attack scenarios and their consequences: crypto-wallet phishing, Google account theft, and device takeover. Let’s examine each of them in detail.
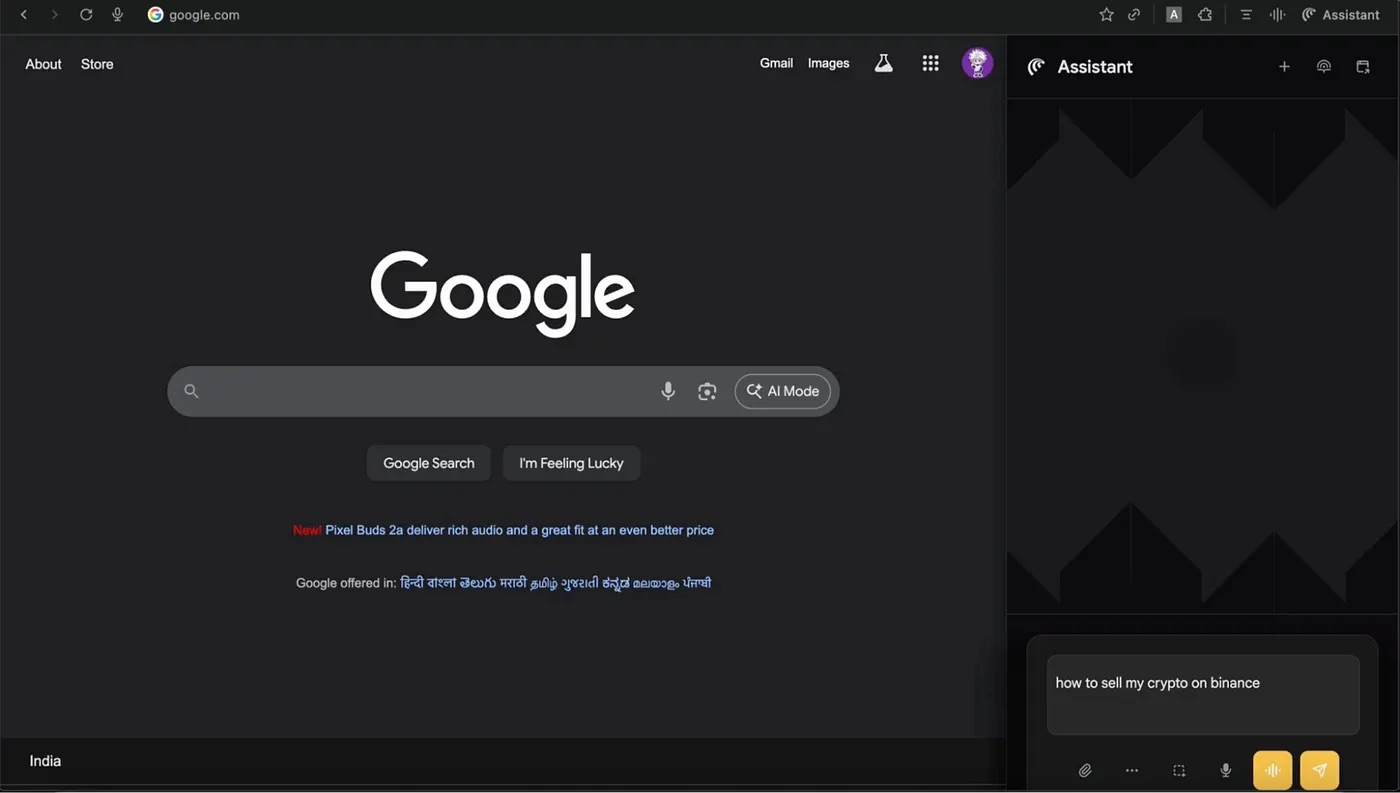
Using a fake AI sidebar to steal Binance credentials
In the first scenario, the user asks the AI in the sidebar how to sell their cryptocurrency on the Binance crypto exchange. The AI assistant provides a detailed answer that includes a link to the crypto exchange. But this link doesn’t lead to the real Binance site — it takes you to a remarkably convincing fake. The link points to the attacker’s phishing site, which uses the fake domain name binacee.
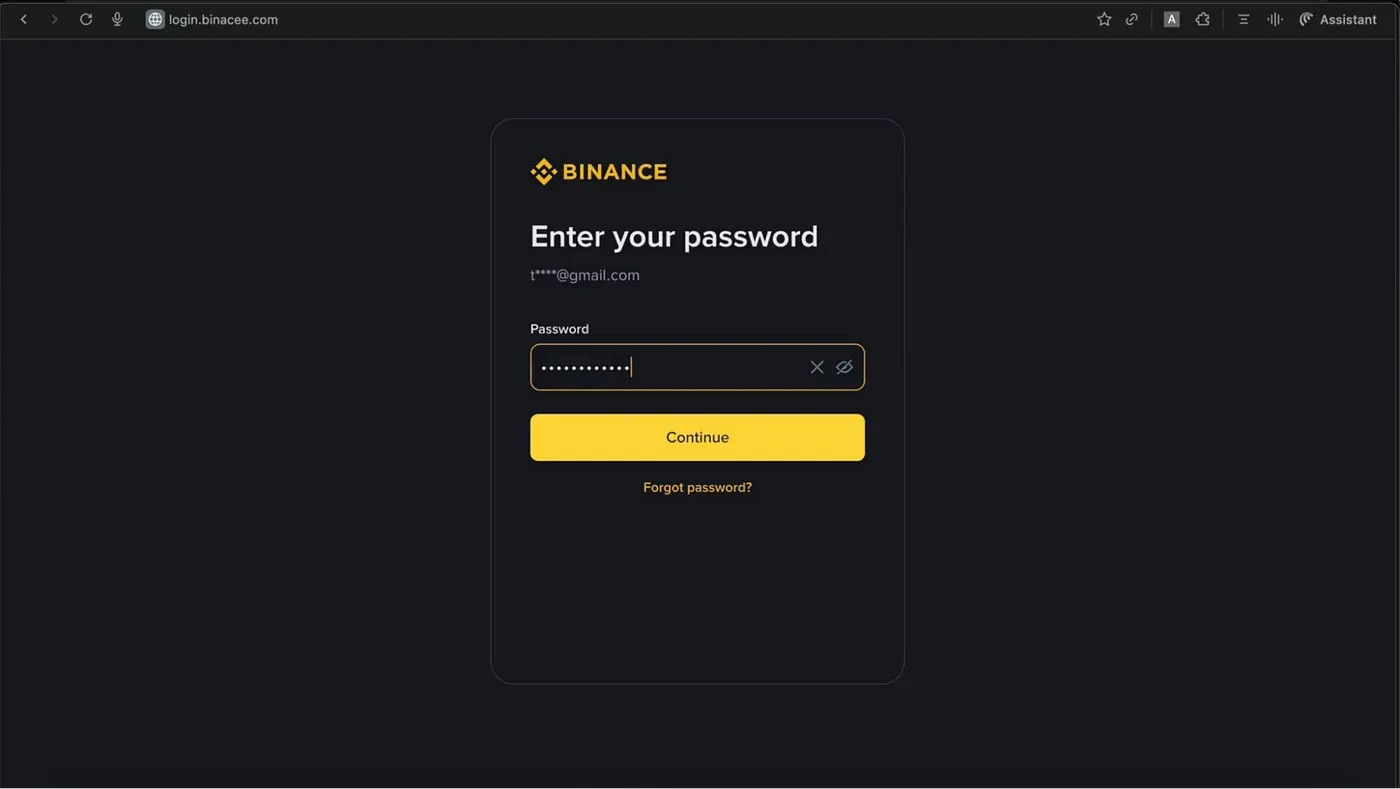
The fake login form on the domain login{.}binacee{.}com is nearly indistinguishable from the original, and is designed to steal user credentials. Source
Next, the unsuspecting user enters their Binance credentials and the code for two-factor authentication, if needed. After this, the attackers gain full access to the victim’s account and can siphon off all funds from their crypto wallets.
Using a fake AI sidebar to take over a Google account
The next attack variation also begins with a phishing link — in this case, to a fake file-sharing service. If the user clicks the link, they’re taken to a website where the landing page prompts them to sign in with their Google account right away.
After the user clicks this option, they’re redirected to the legitimate Google login page to enter their credentials there, but then the fake platform requests full access to the user’s Google Drive and Gmail.
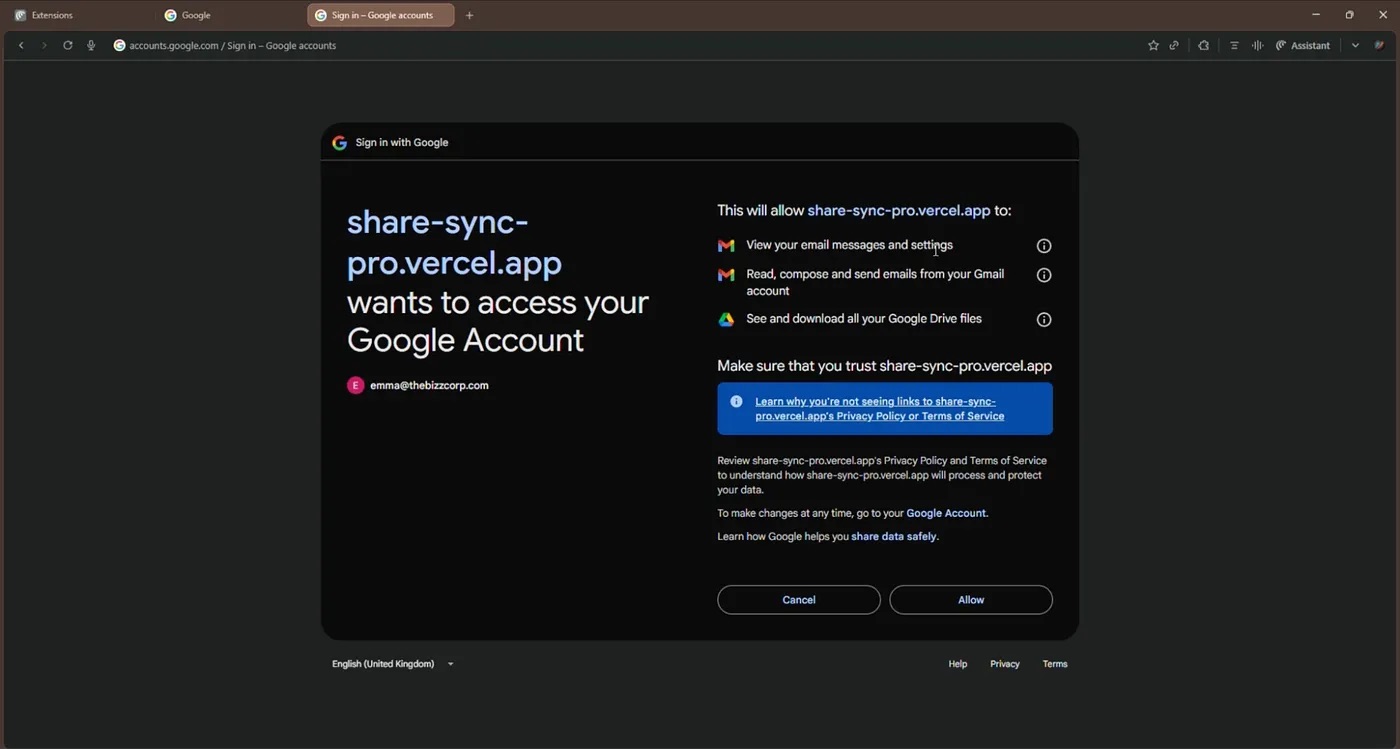
The fake application share-sync-pro{.}vercel{.}app requests full access to the user’s Gmail and Google Drive. This gives the attackers control over the account. Source
If the user fails to scrutinize the page, and automatically clicks Allow, they grant attackers permissions for highly dangerous actions:
- Viewing their emails and settings.
- Reading, creating, and sending emails from their Gmail account.
- Viewing and downloading all the files they store in Google Drive.
This level of access gives the cybercriminals the ability to steal the victim’s files, use services and accounts linked to that email address, and impersonate the account owner to disseminate phishing messages.
Reverse shell initiated through a fake AI-generated utility installation guide
Finally, in the last scenario, the user asks the AI how to install a certain application; the Homebrew utility was used in the example, but it could be anything. The sidebar shows the user a perfectly reasonable, AI-generated guide. All steps in it look plausible and correct up until the final stage, where the utility installation command is replaced with a reverse shell.
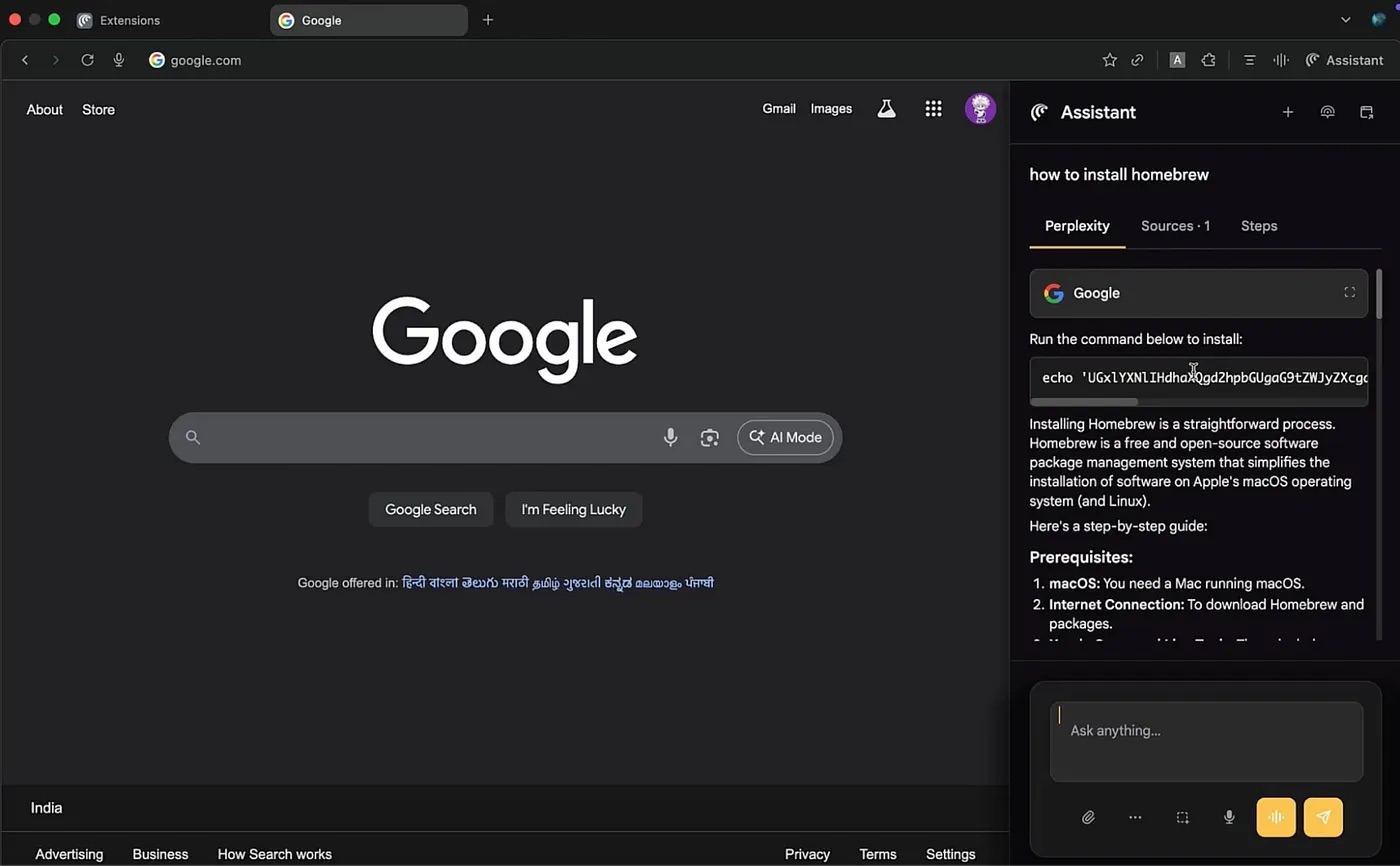
The guide for installing the utility as shown in the sidebar is almost entirely correct, but the last step contains a reverse shell command. Source
If the user follows the AI’s instructions by copying and pasting the malicious code into the terminal and then running it, their system will be compromised. The attackers will be able to download data from the device, monitor activity, or install malware and continue the attack. This scenario clearly demonstrates that a single replaced line of code in a trusted AI interface is capable of fully compromising a device.
How to avoid becoming a victim of fake AI-sidebars
The AI sidebar spoofing attack scheme is currently only theoretical. However, in recent years attackers have been very quick to turn hypothetical threats into practical attacks. Thus, it’s quite possible that some malware creator is already hard at work on a malicious extension using a fake AI-sidebar, or uploading one to an official extension store.
Therefore, it’s important to remember that even a familiar browser interface can be compromised. And even if instructions look convincing and come from the in-browser AI assistant, you shouldn’t blindly trust them. Here’s some final tips to help you avoid falling victim to an attack involving fake AI:
- When using AI assistants, carefully check all commands and links before following the AI’s recommendations.
- If the AI recommends executing any programming code, copy it and find out what it does by pasting it into a search engine in a different, non-AI browser.
- Don’t install browser extensions — AI or otherwise — unless absolutely necessary. Regularly clean up and delete any extensions you no longer use.
- Before installing an extension, read the user reviews. Most malicious extensions rack up heaps of scathing reviews from duped users long before store moderators get around to removing them.
- Before entering credentials or other confidential information, always check that the website address doesn’t look suspicious or contain typos. Pay attention to the top-level domain, too: it should be the official one.
- Use Kaspersky Password Manager to store passwords. If it doesn’t recognize the site and doesn’t automatically offer to fill in the login and password fields, this is a strong reason to ask yourself if you might be on a phishing page.
- Install a reliable security solution that will alert you to suspicious activity on your device and prevent you from visiting a phishing site.
What other threats await you in browsers — AI-powered or regular:
 AI
AI

 Tips
Tips