What happens when spyware is developed not by underground malware coders, but by a serious IT firm? The result can be a nasty thing like FinSpy (also known as FinFisher), which has been developed and sold perfectly legally for quite some time now. Over the past year, we’ve detected this spyware on dozens of mobile devices.
What FinSpy gets up to
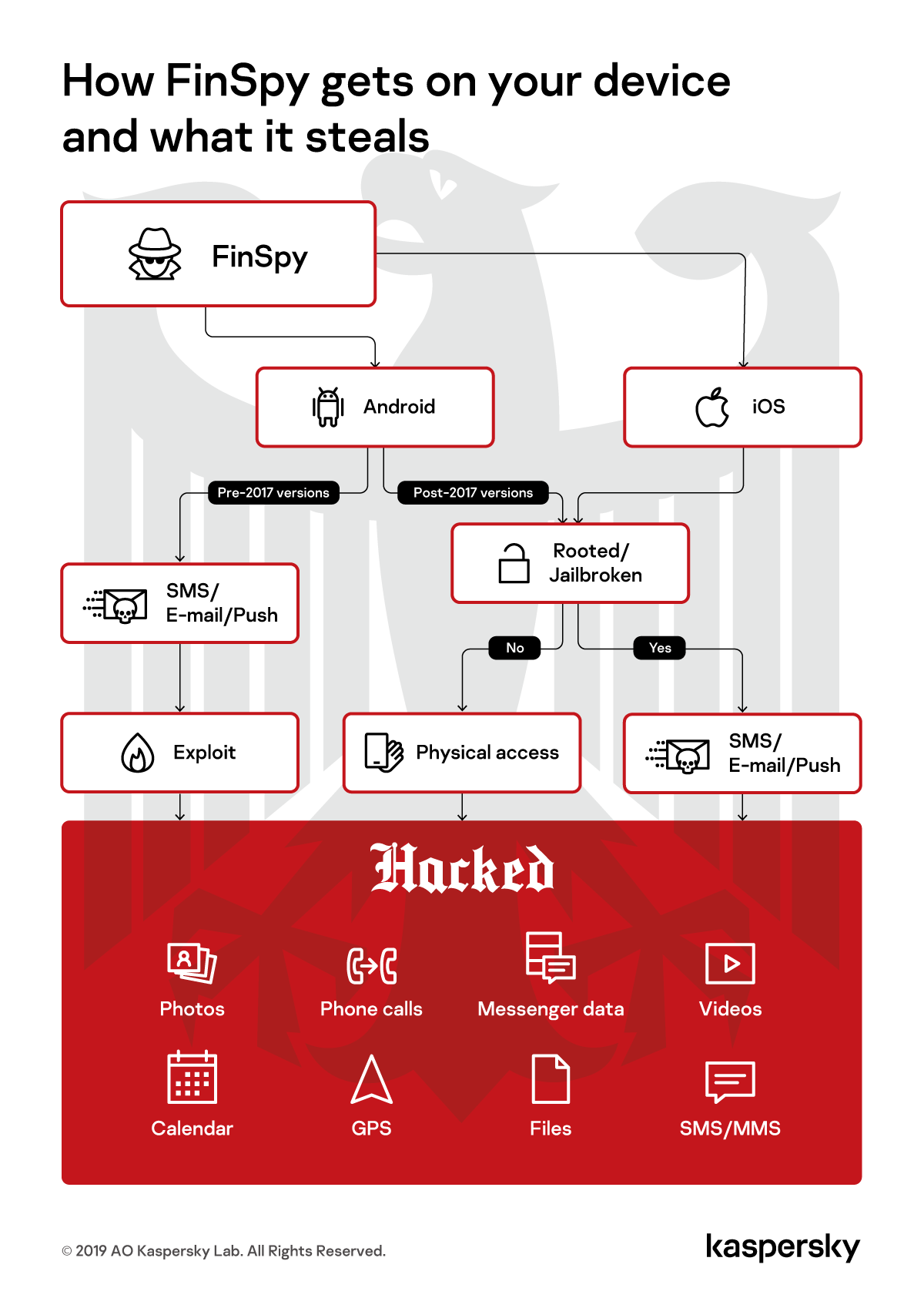
Although a desktop version of the spyware exists (not only for Windows, but also for macOS and Linux), the greatest danger largely comes from mobile implants: FinSpy can be installed on both iOS and Android, with the same set of functions available for each platform. The app gives an attacker almost total control over the data on an infected device.
The malware can be configured individually for each victim and in such a way that provides the attack mastermind with detailed information about the user, including contacts, call history, geolocation, texts, calendar events, and so on.
But that’s not all. FinSpy can record voice and VoIP calls, and intercept instant messages. It has the ability to eavesdrop on many communication services — WhatsApp, WeChat, Viber, Skype, Line, Telegram, as well as Signal and Threema. Besides messages, FinSpy extracts files sent and received by victims in messaging apps, as well as data about groups and contacts. More details about FinSpy are available on Securelist.
Who should beware of FinSpy
Getting infected with FinSpy happens the same as with most types of malware. It’s most often a case of clicking a link in a malicious e-mail or text message.
Android device owners are traditionally in the risk zone, and if their gadgets are also rooted, that greatly facilitates the task of the malware. If, however, the user does not have root access, but a rooting app is installed on the smartphone (as happens when superuser rights are required for installation of some other app), FinSpy can exploit this to obtain the root. Even if a smartphone isn’t rooted, and it has no rooting apps installed, the spyware can get root access using the DirtyCow exploit.
Apple users have a slightly easier time. The iOS version of the spyware requires a system jailbreak. If by some chance the iPhone/iPad owner already did it, the device can be infected in the same way as an Android gadget. But if not, the attacker needs to gain physical access to the device, jailbreak it manually, and then install FinSpy.
How to guard against FinSpy
To avoid falling victim to FinSpy and similar spyware, you need to follow the standard guidelines:
- Do not follow suspicious links in e-mails, instant messages, or text messages.
- Do not try to gain root access (Android) or perform a jailbreak (iOS) on devices that have access to critical data.
- Use a reliable security solution able to detect this type of threat; iPhone owners should bear in mind that unfortunately there are no such solutions for iOS (and here’s why).
 spyware
spyware

 Tips
Tips