Experienced gamers are well aware of the risks of downloading games, mods, skins, and other gaming software from unofficial sources. However, infections can also originate from platforms users typically trust — developer websites and official stores.
In this post, we review several cases where attackers distributed malware through official gaming resources. We also explain how to protect your system, loot, and account — so you can keep playing on your favorite platforms without any nasty surprises.
Infected Endgame Gear mouse-configuration tool
In July 2025, Endgame Gear, a manufacturer of advanced mice aimed at esports players and seasoned gamers, reported a malware infection in its OP1w 4k v2 mouse-config utility. The Trojan remained on the company’s official site for almost two weeks, from June 26 to July 9, 2025.
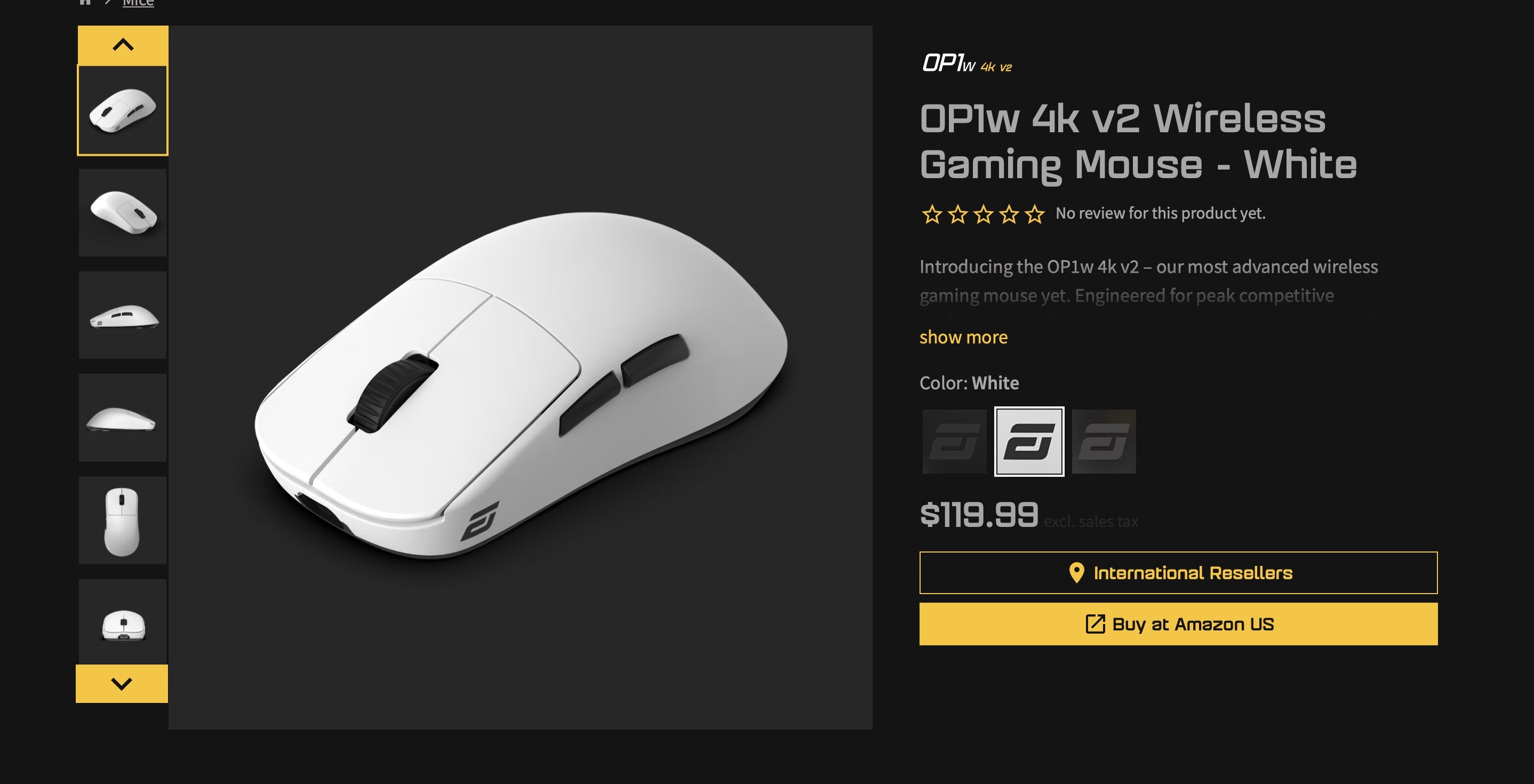
The official page for the Endgame Gear OP1w 4k v2 mouse hosted a malware-infected setup tool. Source
As a result, users who downloaded the utility from the product page during that period also received malware with it. Endgame Gear did not specify what the malicious payload was, but user-scan data suggests it was an XRed backdoor.
XRed offers a wide range of capabilities for remote control of infected systems. These include a keylogger and enables attackers to access the command line, browse disks and folders, download and delete files, and take screenshots. XRed can also download additional modules and exfiltrate system data to remote servers.
It was gamers themselves who first noticed something was wrong with the OP1w 4k v2 configuration tool. They began discussing suspicious signs on Reddit nearly two weeks before Endgame Gear released an official statement. The key details that raised user suspicions were the size of the program — the infected version was 2.8MB instead of the usual 2.3MB — and the file signature, listed as “Synaptics Pointing Device Driver” instead of “Endgame Gear OP1w 4k v2 Configuration Tool”.
In its official statement on the incident, Endgame Gear clarified that users who downloaded the tool from the general downloads page (endgamegear.com/downloads), GitHub, or the company’s Discord channel are safe. The threat only affected gamers who downloaded software directly from the OP1w 4k v2 product page between June 26 and July 9, 2025. After that, the malware was removed from the company’s site.
The mouse manufacturer recommends the following steps for any potentially affected users:
- Delete all contents of the folder C:ProgramDataSynaptics.
- Run a full system scan with a reliable antivirus.
- Download a clean version of the utility.
In addition, users should change passwords for all important accounts, including financial services, email, and work-related logins.
Malware in three early-access Steam games
In 2025, several cases were reported of malware being distributed through early-access games on Steam.
- In February, this involved PirateFi, a survival sim (we covered this case on the Kaspersky Daily blog).
- In March, a similar incident occurred with the tactical shooter Sniper: Phantom’s Resolution.
- In July, attackers uploaded an infected version of Chemia, another survival game.
All three cases involved early-access titles — likely because Steam applies looser verification procedures for pre-release games. Let’s take a closer look at these three cases.
A few days after the beta release of PirateFi — the first game developed by a studio called Seaworth Interactive — one user reported on a Steam forum that his antivirus had prevented the game from launching. The security software detected the presence of Trojan.Win32.Lazzzy.gen malware, which the game attempted to install in the AppData/Temp directory after launch.
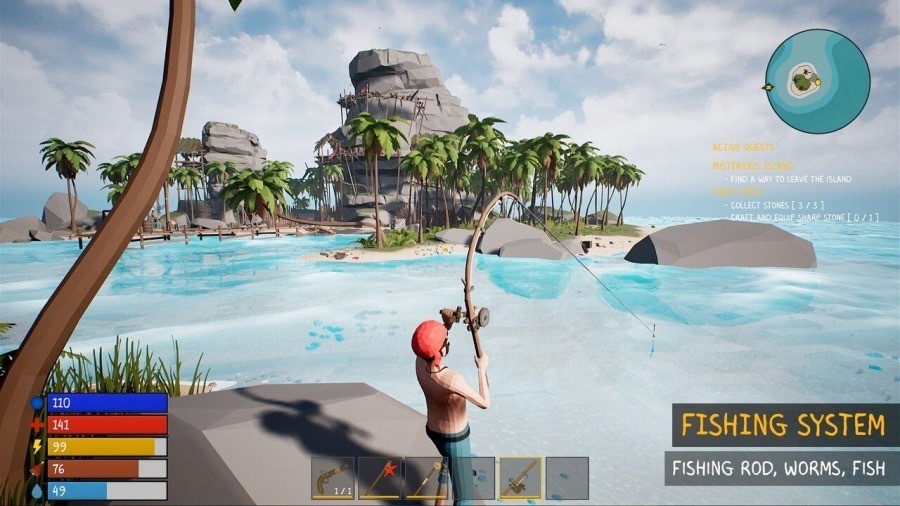
PirateFi promised players a pirate-themed survival sim, but in reality it stole browser cookies to hijack accounts. Source
The Trojan’s primary goal was to steal browser cookies. These cookies allowed the attackers to access victims’ accounts for financial services, social networks, and other online platforms. Several players who downloaded and ran the game reported that the criminals changed the passwords on their accounts and stole funds. PirateFi was pulled from Steam just four days after release. All users who had downloaded the game — fortunately, only around 800 people — received an official notification from the platform warning them of the malware on their devices.
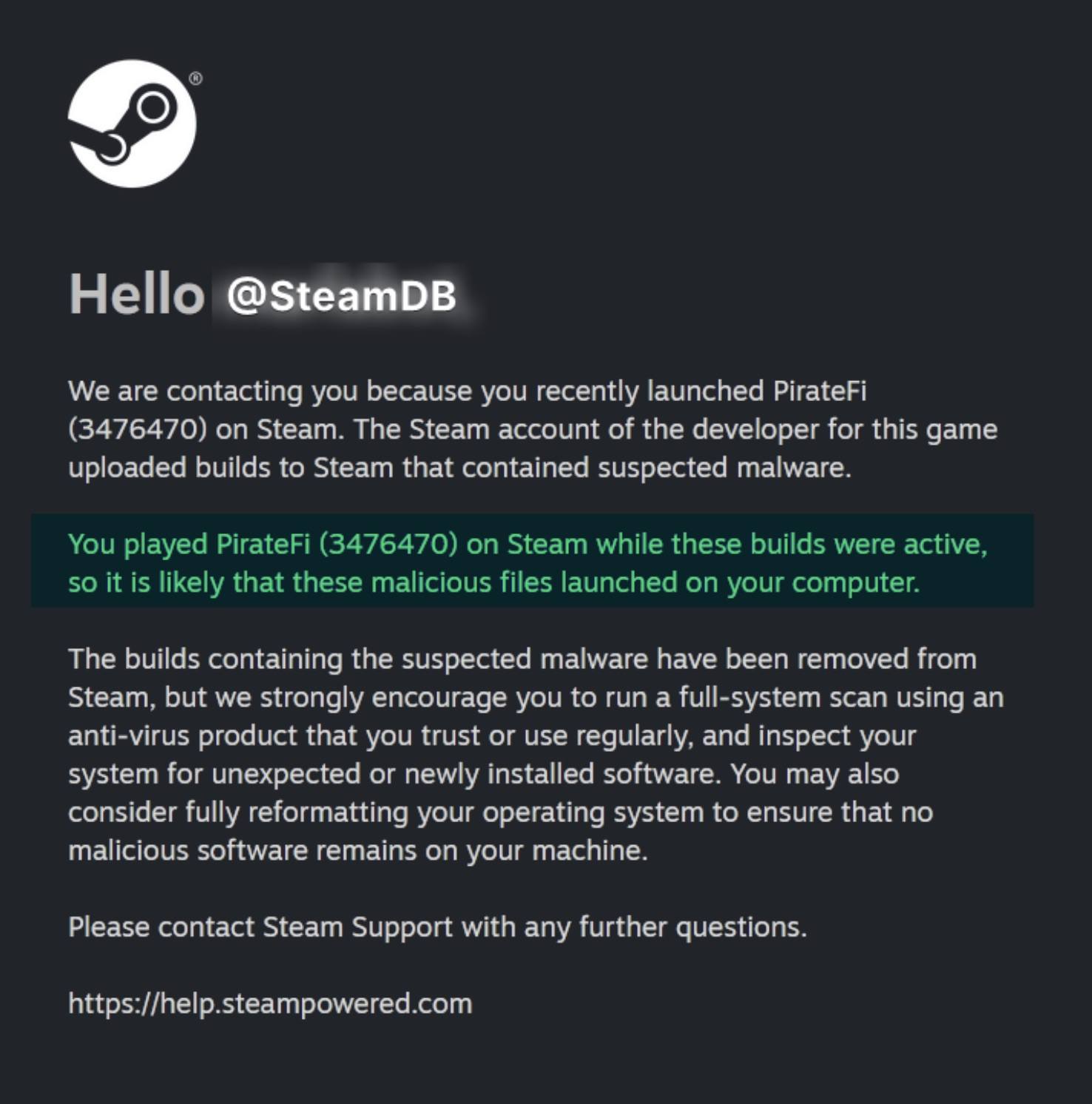
Steam users who downloaded the infected PirateFi game were warned of malware on their devices. Source
Just a month later, a similar situation occurred with another game — Sniper: Phantom’s Resolution by Sierra Six Studios. Once again, players were the first to suspect something was wrong: they noticed that the game’s description and screenshots were clearly copied from other projects. Another red flag was the developer’s offering a demo installer hosted on an external GitHub repository rather than through Steam.
Further examination of the installer’s code by Reddit users revealed suspicious software hidden inside. Like the creators of PirateFi, those behind Sniper: Phantom’s Resolution seemed to be after victims’ online accounts. Following user reports, both GitHub and Steam quickly removed the malicious game from their platforms.
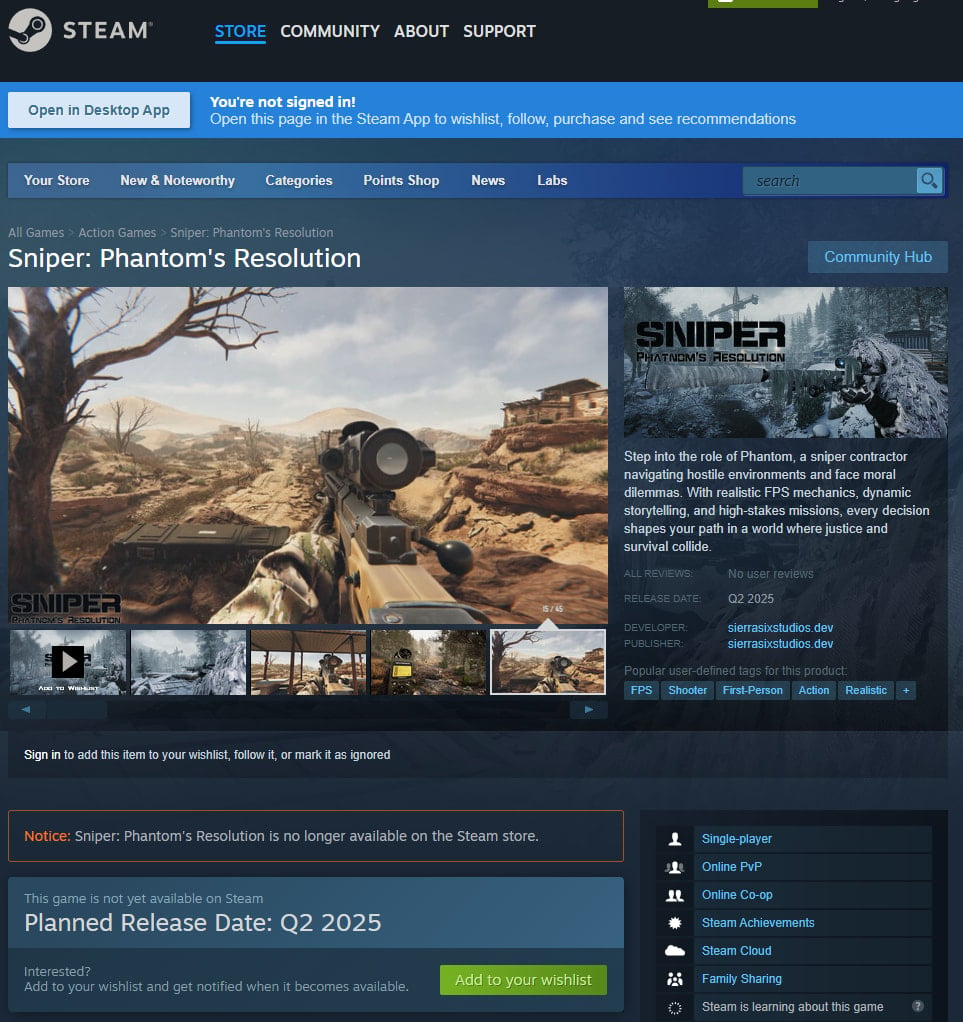
The game Sniper: Phantom’s Resolution was published on Steam with an installer containing malware, and was removed after user complaints. Source
The third case, involving a game called Chemia by Aether Forge Studios, was a little different: this time, it was a beta version of a legitimate game that was infected. Cybersecurity researchers believe the attack was carried out by the hacker group EncryptHub, also known as Larva-208.
It remains unclear how the attackers managed to inject malware into the game. However, players who launched the Chemia playtest unknowingly downloaded two infostealers to their devices. Both ran silently in the background without affecting gameplay, leaving gamers unaware their systems were compromised.
The Chemia playtest on Steam was distributed with infostealing malware that ran in the background, extracting data from browsers. Source
The attackers were targeting data stored in browsers, including saved passwords, autofill info, cookies, and cryptowallet details. At the time of writing, the game is no longer available on Steam. However, neither the platform nor the game’s developer has issued an official statement.
Malicious skins on the official Minecraft website
Sometimes dangers lurk not just on Steam, but also on developers’ official sites — including the biggest names. In 2018, about fifty thousand Minecraft players fell victim to attackers who uploaded malicious skins to the official Minecraft website. That platform has a fan-interaction system where any player can share skins they create with others — and that’s what the attackers exploited.

The Minecraft skins that could reformat hard drives and delete system programs. Source
The malware was spread via PNG skin files, and was capable of deleting programs, formatting hard drives, and destroying backup data. One peculiar detail was that some victims received bizarre messages with titles such as:
- “You Are Nailed, Buy A New Computer This Is A Piece Of Sh*t”,
- “You have maxed your internet usage for a lifetime”,
- “Your a** got glued.”
The malicious code’s specifics make experts believe that professional cybercriminals were likely not behind the attack. Still, the Minecraft case clearly demonstrated the vulnerability of content-sharing mechanisms on gaming platforms.
How to avoid becoming a victim
Installing games, mods, skins, and other gaming software from official sources is, of course, safer than pirating them from shady ones. However, as we’ve shown in this post, even legitimate sites require vigilance.
- Read reviews carefully before downloading any game or gaming software. Do a quick background check — a simple search might lead you to a Reddit thread discussing suspicious issues.
- Be cautious with early-access games on Steam. Three malicious games in a single year already signals a trend.
- Install reliable protection on your device.
Many gamers may be skeptical about this last tip, as it’s a common belief in the gaming community that antivirus software slows down games. That may have been true years ago, but tests these days show that the latest security solutions cause no measurable drops in performance.
Moreover, Kaspersky Premium even includes a dedicated gaming mode. It turns on automatically when a game launches, postponing database updates, notifications, and routine scans until the session ends — thus minimizing system resource usage.
How else do attackers target gamers? Check out our selection of articles on this topic:
 gamers
gamers
