Not much on the face of it, as cybercrime hadn’t been invented when Indiana was busy getting the better of agents of the Soviet Union, Nazis, Chinese gangsters, and other enemies with cunning and style. However, he was an archaeologist and here the similarities are clear.
Archaeologists are highly skilled at taking bare bones or pieces of artefact and digging deeper and deeper to expose further clues and discover more. Cybersecurity experts start with a few lines of code or a single threat and, like Indiana, use their expertise to relentlessly track, analyse and decipher until they have a detailed picture of the attackers and their methods.
The global threat landscape
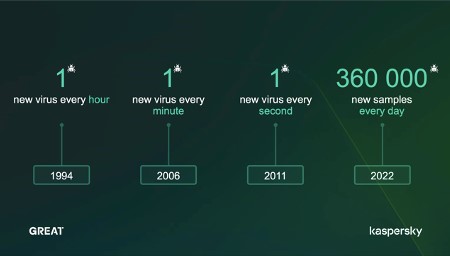
Cybercrime became a problem in the 1990s and developed steadily at first. However, it’s exploded in scale and severity in recent years, as increasingly complex environments expand attack surfaces and threat actors become ever more sophisticated. One of the key changes to the threat landscape in the past 30 years is highlighted in these startling statistics:
Opportunist cybercriminals are not the only hackers to exploit the world’s dependence on technology. Organised groups and nation-state sponsored attackers are also increasingly launching targeted campaigns. Known as Advanced Persistent Threats (APTs), these are highly sophisticated and difficult to predict and detect.
Today, cyber-attacks pose a huge risk to consumers, organisations and governments worldwide. According to the Chair of the US Federal Reserve, Jerome Powell, it’s currently the biggest concern for the economy and successful attacks could paralyse parts of the financial system, anywhere in the world.
“The risk that we keep our eyes on most now is cyber risk” – Jerome Powell, US Federal Reserve Chair.
The ongoing conflict in Ukraine has underlined the potential impact of cyber-attacks, as threat actors involved in the conflict step up malicious activity in support of the belligerent parties. It comes at no surprise that western cybersecurity agencies, including in the UK, have recently warned of a possible rise in attacks. Criminals target businesses as well as governments and infrastructure through increasingly sophisticated methods and the problem is already global.
So, we need a worldwide response, proactive rather than reactive and involving all the key players in international cybersecurity.
Intelligent threats call for Threat intelligence
This is where Threat Intelligence comes in.
Threat Intelligence is the evidence-based process of identifying and analysing current and future cyberthreats. Information is gathered from multiple sources, then sifted, analysed and organised; patterns are spotted, trends defined, and threat actors uncovered. Intelligence may include an individual threat’s origin, coding, modifications, delivery, and potential damage. This invaluable intelligence helps organisations to plan, mitigate and prevent: to be proactive.
It’s not just about amassing data. You also need the bigger picture – and the data is only valuable if you have the context and the finer details – to inform your strategic security decisions, fast. Many organisations make the mistake of relying on raw data.
Kaspersky’s GReAT experts
Kaspersky has led the way in threat research for 25 years. We have petabytes of rich data to mine, advanced machine learning technologies and a unique pool of global experts. Here’s a snapshot of the latest on what we know about current threats:
How do we know this?
Meet our Global Research and Analysis (GReAT) team of almost 40 experts from all over the world. Operating at the very heart of Kaspersky, they unearth APTs, cyber espionage campaigns, major malware, ransomware, and underground cybercriminal trends, right across the globe. They have unrivalled expertise, they’re passionate, tenacious and they’re curious.
Focusing on millions of objects every day, the team uses machine learning and human updates to recognise and predict threats. Sources include APT research, partner research, bot farms, web crawlers, open source, and dark web material. They analyse code and the language used is key to understanding the threat and the actors behind it.
There are no restrictions on GReAT’s work. Our experts examine and report on all the threats that they find, regardless of their origin. They are free to explore and go off at tangents: to find out as much as they can. To adapt the archaeological analogy, they are the high-tech version of palaeontologists, fascinated by malicious code (rather than fossils and skeletons) and always digging deeper to uncover more and more about the nature of the beast.

As a palaeontologist examines bones to build a complete picture of a Tyrannosaurus Rex, our researchers analyse code to identify and contextualise threats.
GReAT publishes intelligence so that organisations worldwide have a clear overview of the latest threats. There’s a symbiotic relationship between the work carried out by GReAT and the tools they use for threat hunting. All data and findings feed into the development process to ensure that our products are up-to-date and as secure as possible; the improved systems in turn enhance GReAT’s threat hunting, and so the loop continues.
Research without borders
Kaspersky is committed to transparency in everything we do. We have set the industry standard with our Global Transparency Initiative, opening Transparency Centres, relocating critical data storage and processing and submitting our internal processes for third party assessment.
Our research has no borders. GReAT is a multinational team, ready to expose any threat, wherever it originates and whatever the language. It has reported on APTs with code written in Russian, English, Korean, Chinese and other languages. Some of the best-known threat actors uncovered by GReAT include: Duqu, Flame, Gauss, Red October, Equation, Regin, Project Sauron and Olympic Destroyer.
The team’s highly skilled forensic work empowers others. Sir Isaac Newton, famed for his theory of universal gravity, wrote in 1675: “If I have seen further than others, it is by standing on the shoulders of giants.” In other words, his work would have been impossible without the pioneering scientists before him. The GReAT experts are delighted that threat hunters across the world similarly stand on their shoulders, harnessing their expertise to uncover cyberthreats.
International co-operation
As we’ve seen, cyberthreats have no borders. Threat actors operate worldwide and can strike anywhere, so international co-operation is vital in the fight against them. Kaspersky and the GReAT team are proud to share our expertise, knowledge and technical findings with the global security community.
For example, we are founding members of No More Ransom, an initiative to educate businesses and protect them from ransomware exploitation, and Coalition Against Stalkerware, working with non-profit organisations, survivors and victims and law enforcement agencies against this form of online abuse. Together, we can help to defeat the cyber-attackers.
If you want to learn more about our approach to Threat Intelligence, or how the GReAT team at Kaspersky work, please don’t hesitate to get in touch through our “Contact us” page.
 threat intelligence
threat intelligence


 Tips
Tips