Modern server processors feature a trusted execution environment (TEE) for handling especially sensitive information. There are many TEE implementations, but two are most relevant to this discussion: Intel Software Guard eXtensions (SGX), and AMD Secure Encrypted Virtualization (SEV). Almost simultaneously, two separate teams of researchers — one in the U.S. and one in Europe — independently discovered very similar (though distinct) methods for exploiting these two implementations. Their goal was to gain access to encrypted data held in random access memory. The scientific papers detailing these results were published just days apart:
- WireTap: Breaking Server SGX via DRAM Bus Interposition is the effort of U.S. researchers, which details a successful hack of the Intel Software Guard eXtensions (SGX) system. They achieved this by intercepting the data exchange between the processor and the DDR4 RAM module.
- In Battering RAM, scientists from both Belgium and the UK also successfully compromise Intel SGX, as well as AMD’s comparable security system, SEV-SNP, by manipulating the data-transfer process between the processor and the DDR4 RAM module.
Hacking a TEE
Both the technologies mentioned — Intel SGX and AMD SEV — are designed to protect data even if the system processing it is completely compromised. Therefore, the researchers began with the premise that the attacker would have complete freedom of action: full access to both the server’s software and hardware, and the confidential data they seek residing, for instance, on a virtual machine running on that server.
In that scenario, certain limitations of both Intel SGX and AMD SEV become critical. One example is the use of deterministic encryption: an algorithm where a specific sequence of input data always produces the exact same sequence of encrypted output data. Since the attacker has full access to the software, they can input arbitrary data into the TEE. If the attacker also had access to the resulting encrypted information, comparing these two data sets would allow them to calculate the private key used. This, in turn, would enable them to decrypt other data encrypted by the same mechanism.
The challenge, however, is how to read the encrypted data. It resides in RAM, and only the processor has direct access to it. The theoretical malware only sees the original information before it gets encrypted in memory. This is the main challenge, which the researchers approached in different ways. One straightforward, head-on solution is hardware-level interception of the data being transmitted from the processor to the RAM module.
How does this work? The memory module is removed and then reinserted using an interposer, which is also connected to a specialized device: a logic analyzer. The logic analyzer intercepts the data streams traveling across all the data and address lines to the memory module. This is quite complex. A server typically has many memory modules, so the attacker must find a way to force the processor to write the target information specifically to the desired range. Next, the raw data captured by the logic analyzer must be reconstructed and analyzed.
But the problems don’t end there. Modern memory modules exchange data with the processor at tremendous speeds, performing billions of operations per second. Intercepting such a high-speed data flow requires high-end equipment. The hardware that was used to prove the feasibility of this type of attack in 2021 cost hundreds of thousands of dollars.
The features of WireTap
The U.S. researchers behind WireTap managed to slash the cost of their hack to just under a thousand dollars. Their setup for intercepting data from the DDR4 memory module looked like this:

Test system for intercepting the data exchange between the processor and the memory module Source
They spent half of the budget on an ancient, quarter-century-old logic analyzer, which they acquired through an online auction. The remainder covered the necessary connectors, and the interposer (the adapter into which the target memory module was inserted) was custom-soldered by the authors themselves. An obsolete setup like this could not possibly capture the data stream at its normal speed. However, the researchers made a key discovery: they could slow down the memory module’s operation. Instead of the standard DDR4 effective speeds of 1600–3200 megahertz, they managed to throttle the speed down to 1333 megahertz.
From there, the steps are… well, not really simple, but clear:
- Ensure that the data from the target process was written to the hacked memory module and then intercept it, still encrypted at this stage.
- Input a custom data set into Intel SGX for encryption.
- Intercept the encrypted version of the known data, compare the known plaintext with the resulting ciphertext, and compute the encryption key.
- Decrypt the previously captured data belonging to the target process.
In summary, WireTap work doesn’t fundamentally change our understanding of the inherent limitations of Intel SGX. It does however demonstrate that the attack can be made drastically cheaper.
The features of Battering RAM
Instead of the straightforward data-interception approach, the researchers from Belgium’s KU Leuven university and their UK colleagues sought a more subtle and elegant method to access encrypted information. But before we dive into the details, let’s look at the hardware component and compare it to the American team’s work:
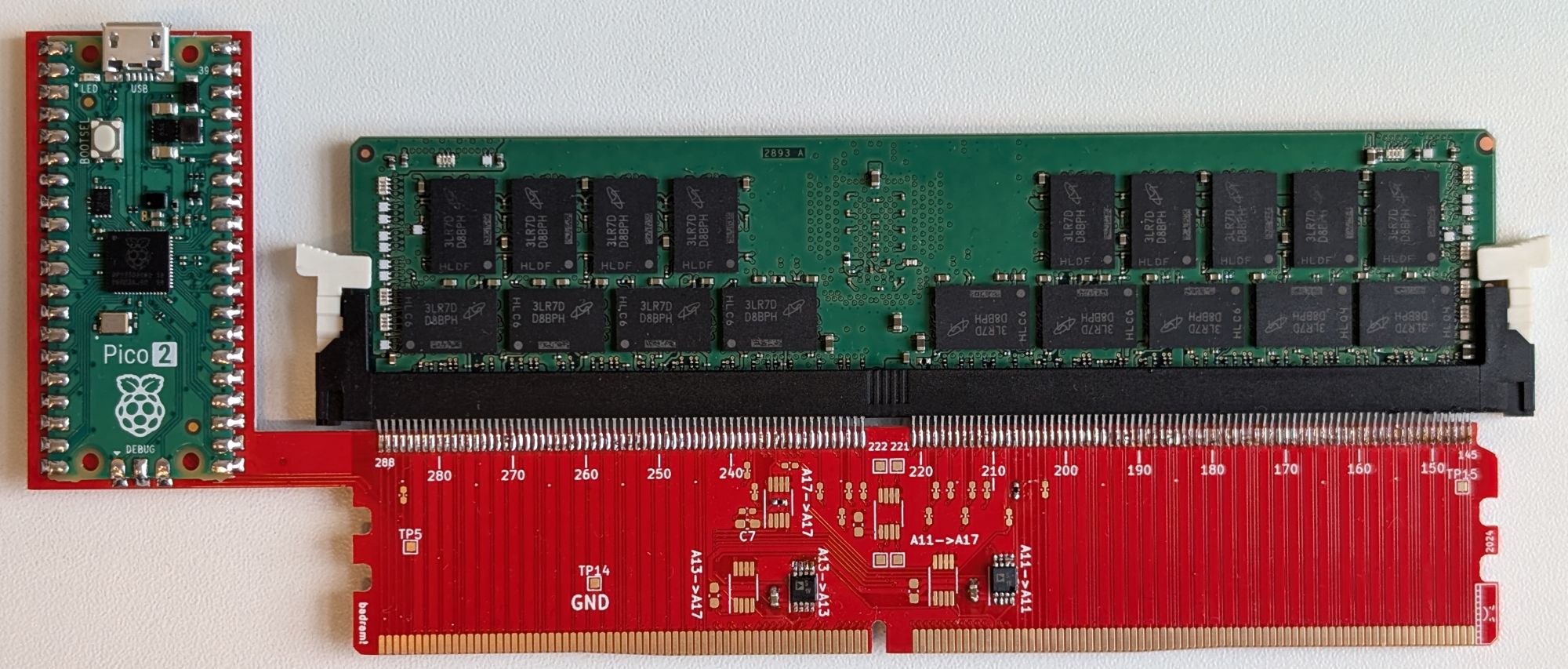
The memory module interposer used in Battering RAMSource
In place of a tangle of wires and a bulky data analyzer, this setup features a simple board designed from scratch, into which the target memory module is inserted. The board is controlled by an inexpensive Raspberry Pi Pico microcomputer. The hardware budget is negligible: just 50 euros! Moreover, unlike the WireTap attack, Battering RAM can be conducted covertly; continuous physical access to the server isn’t needed. Once the modified memory module is installed, the required data can be stolen remotely.
What exactly does this board do? The researchers discovered that by grounding just two address lines (which dictate where information is written or read) at the right moment, they could create a data mirroring situation. This causes information to be written to memory cells that the attacker can access. The interposer board acts as a pair of simple switches controlled by the Raspberry Pi microcomputer. While manipulating contacts on live hardware typically leads to a system freeze or data corruption, the researchers achieved stable operation by disconnecting and reconnecting the address lines only at the precise moments required.
This method gave the authors the ability to select where their data was recorded. Crucially, this means they didn’t even need to compute the encryption key! They first captured the encrypted information from the target process. Next, they ran their own program within the same memory range and requested the TEE system to decrypt the previously captured information. This technique allowed them to hack not only Intel SGX but also AMD SEV. Furthermore, this control over data writing helped them circumvent AMD’s security extension called SEV-SNP. This extension, using Secure Nested Paging, was designed to protect the virtual machine from compromise by preventing data modification in memory. Circumventing SEV-SNP theoretically allows attackers not only to read encrypted data but also to inject malicious code into a compromised virtual machine.
The relevance of physical attacks on server infrastructure
It’s clear that while the practical application of such attacks is possible, they’re unlikely to be conducted in the wild. The value of the stolen data would need to be extremely high to justify hardware-level tampering. At least, this is the stance taken by both Intel and AMD regarding their security solutions: both chipmakers responded to the researchers by stating that physical attacks fall outside their security model. However, both the American and European research teams demonstrated that the cost of these attacks is not nearly as high as previously believed. This potentially expands the list of threat actors willing to utilize such complex vulnerabilities.
The proposed attacks do come with their own restrictions. As we already mentioned, the information theft was conducted on systems equipped with DDR4 standard memory modules. The newer DDR5 standard, finalized in 2020, has not yet been compromised, even for research purposes. This is due both to the revised architecture of the memory modules and their increased operating speeds. Nevertheless, it’s highly likely that researchers will eventually find vulnerabilities in DDR5 as well. And that’s a good thing: the declared security of TEE systems must be regularly subjected to independent audits. Otherwise, it could turn out at some point that a supposedly trusted protection system unexpectedly becomes completely useless.
 RAM
RAM

 Tips
Tips