As targeted ransomware continues to haunt businesses all over the globe, one can’t help but look deeper into the operations of particular ransomware gangs.
As targeted ransomware continues to haunt businesses all over the globe, one can’t help but look deeper into the operations of particular ransomware gangs. This helps to better understand them and develop more advanced protection against the threats they pose. Kaspersky researchers took apart and inspected a curious specimen (or, more correctly, specimens) belonging to the JSWorm group, which demonstrated its agility when it comes to upgrading its toolset. The group, which has previously focused on mass-scale operations, was able to quickly adapt and evolve into a highly-targeted operation in just two years, developing over eight distinct malware ‘brand names’.
Each ‘rebranded’ variant had different aspects of the code, renamed file extensions, cryptographic schemes and encryption keys altered. Together with name changes, the developers of this ransomware have also been reworking their code and trying different approaches to distribution, which shows they are highly adaptivity and have vast resources at hand.
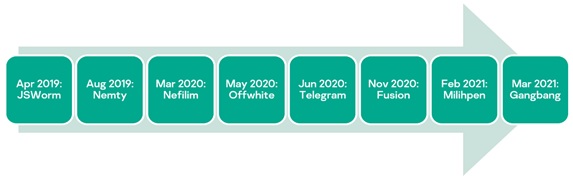
The most notable versions of ransomware created by the JSWorm developers
JSWorm has been detected across the globe – from North and South America (Brazil, Argentina, USA) to the Middle East and Africa (South Africa, Turkey, Iran), Europe (Italy, France, Germany), and APAC (Vietnam), with more than a third (39%) of of all the enterprises and individuals this group targeted in 2020 located in APAC.
When it comes to target industries, it is clear that this ransomware family eyes critical infrastructure and major sectors across the world. Nearly half (41%) of JSWorm attacks were targeted against companies in the Engineering and Manufacturing industry. Energy and Utilities (10%), Finance (10%), Professional and Consumer Services (10%), Transportation (7%), and Healthcare (7%) were also at the top of their list.
“JSWorm’s operations, and its ability to adapt and develop new malware so quickly, reflects an important and worrying trend – ransomware gangs have more than enough resources at their disposal to change their operations and upgrade their toolsets at a disturbing speed, tackling more and more organisations across the world. Such high adaptiveness is usually seen among APT groups, but ransomware gangs are not limited to specific targets, they will happily go after any company they would be able to infect. This demonstrates that to protect one’s organisation, cybersecurity teams need to become even faster, more attentive and adaptive when it comes to installing security measures,” comments Fedor Sinitsyn, security researcher at Kaspersky.
Read the full report about the different versions of JSWorm on Securelist. Learn more about the ransomware ecosystem in the Ransomware world in 2021: who, how and why report.
To remain protected against JSWorm and other types of ransomware, Kaspersky recommends:
- Not exposing remote desktop services (such as RDP) to public networks unless absolutely necessary and always use strong passwords for them.
- Making sure commercial VPN solutions and other server-side software are always up to date as exploitation of this type of software is a common infection vector for ransomware. Always keep client-side applications up to date as well.
- Focusing your defense strategy on detecting lateral movements and data exfiltration to the internet. Pay special attention to the outgoing traffic to detect cybercriminal connections. Back up data regularly. Make sure you can quickly access it in an emergency when needed. Use the latest Threat Intelligence information to stay aware of actual TTPs used by threat actors.
- Using solutions like Kaspersky Endpoint Detection and Response and the Kaspersky Managed Detection and Response service to help identify and stop an attack at the early stages, before the attackers achieve their ultimate goals.
- Protecting the corporate environment and educating your employees. Dedicated training courses can help, such as those provided in the Kaspersky Automated Security Awareness Platform.
- Using a reliable endpoint security solution, such as Kaspersky Endpoint Security for Business that is powered by exploit prevention, behavior detection and a remediation engine that is able to roll back malicious actions. KESB also has self-defense mechanisms that can prevent its removal by cybercriminals.
About Kaspersky
Kaspersky is a global cybersecurity and digital privacy company founded in 1997. Kaspersky’s deep threat intelligence and security expertise is constantly transforming into innovative security solutions and services to protect businesses, critical infrastructure, governments and consumers around the globe. The company’s comprehensive security portfolio includes leading endpoint protection and a number of specialised security solutions and services to fight sophisticated and evolving digital threats. Over 400 million users are protected by Kaspersky technologies and we help 240,000 corporate clients protect what matters most to them. Learn more at www.kaspersky.com.
