In early August 2010, the first-ever malicious program for the Android operating system was detected: the SMS Trojan FakePlayer
Please see below the latest findings from Kaspersky Lab’s monthly malware report.
For further information, or to speak to a Kaspersky Lab spokesperson, please contact us on kasperskylab@berkeleypr.co.uk or 01189 090909.
Attacks against individual users: mobile threats
In early August 2010, the first-ever malicious program for the Android operating system was detected: the SMS Trojan FakePlayer. Today, threats designed for Android represent approximately 23% of the overall number of detected threats targeting mobile platforms.
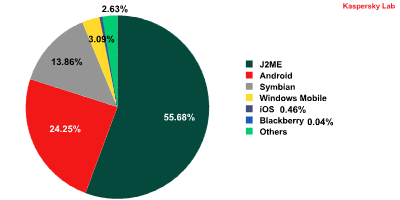
The distribution of malicious programs targeting mobile platforms, by operating system
Excluding the J2ME platform, 85% of the total number of smartphone threats detected during August 2010 targeted the Android system.
In August, the Nickspy Trojan stood out among the multitude of threats targeting mobile platforms. Its distinguishing characteristics include an ability to collect information about the phone’s GPS coordinates and any calls that are made from the device. It can also record all the conversations that the infected device’s owner has. The audio files are then uploaded to a remote server managed by the malicious owner.
Out-of-the-box activity
Malware and Bitcoin. As of late August, Kaspersky Lab’s analysts detected 35 unique malicious programs that targeted the Bitcoin system in one way or another. Realising that their potential earnings largely depend on the number of computers they have access to, the cybercriminals have moved from stealing Bitcoin wallets to using Twitter and P2P network-based botnets. Cybercriminals have resorted to this measure to counter the antivirus companies that may block the operation of a single botnet C&C server if no alternate servers exist in the malicious network. For example, a bot would send a request to a Twitter account, which provides commands that are left there by the botnet owner — i.e., where the Bitcoin-generating program is downloaded, along with instructions for which Bitcoin pools to work with. The use of Twitter as a botnet command centre is not new; although this is the first time it has been used with the Bitcoin system.
Ice IX: the illegitimate child of ZeuS. Almost a year after the original code of the most wide-spread threat targeting online banking users was leaked, Trojan ZeuS, Russian-speaking cybercriminals created its clone which became quite popular among fraudsters this summer. The new variant which emerged in the spring was dubbed Ice IX by its creator and sells for US $600-1,800. One of Ice IX’s most remarkable innovations is the altered botnet control web module which allows cybercriminals to use legitimate hosting services instead of costly bulletproof servers maintained by the cybercriminal community. This difference is meant to keep hosting costs down for Ice IX owners. The appearance of Ice IX indicates that the industry should soon expect the emergence of new “illegitimate children” of ZeuS and an even greater number of attacks against the users of online banking services.
Remote-access worm. The new network worm Morto is interesting in that it does not exploit vulnerabilities in order to self-replicate. Furthermore, it spreads via the Windows RDP service that provides remote access to a Windows desktop – a method which has not been seen before. Essentially, the worm attempts to find the access password. Provisional estimates indicate that tens of thousands of computers throughout the globe may currently be infected with this worm.
Attacks against the networks of corporations and major organisations The IT community was shaken by a news item from McAfee about their detection of what was potentially the largest cyber-attack in history, lasting over five years and targeting numerous organisations around the world, from the US Department of Defense, to the Sports Committee of Vietnam. The attack was dubbed Shady Rat. All would have been well and good, but the malicious user-run server that was allegedly “detected by researchers” had in fact already been known to the experts at many other antivirus companies for several months. Moreover, at the time of the article’s publication the server was still up and running and all of the information that McAfee used in its report had already been made public. What is more, the long sought-after spyware that had allegedly been used in the most complex and largest attack in history had already been detected by many antivirus programs using simple heuristics. In addition to these and other factors, the McAfee incident gives rise to many other questions, which were asked publically, including by Kaspersky Lab’s experts.
“Our studies have confirmed that Shady Rat was not the longest-running or the largest, nor even the most sophisticated attack in history”, comments Alexander Gostev, Chief Security Expert at Kaspersky Lab. “Moreover, we believe that it is unacceptable to publish information about any attacks without a full description of all of the components and technologies used, since these incomplete reports do not allow experts to make all possible efforts to protect their own resources.”
Kaspersky Lab Newsroom
Kaspersky Lab has launched a new online newsroom, Kaspersky Lab Newsroom Europe (http://newsroom.kaspersky.eu/en), for journalists throughout Europe. The newsroom is specifically designed to serve many of the media’s most common requests, making it easier for journalists to find product and corporate information, facts and figures, editorial copy, images, videos and audio files, as well as details about the appropriate PR contacts.
About Kaspersky Lab
Kaspersky Lab is the largest antivirus company in Europe. It delivers some of the world’s most immediate protection against IT security threats, including viruses, spyware, crimeware, hackers, phishing, and spam. The company is ranked among the world’s top four vendors of security solutions for endpoint users. Kaspersky Lab products provide superior detection rates and one of the industry’s fastest outbreak response times for home users, SMBs, large enterprises and the mobile computing environment. Kaspersky® technology is also used worldwide inside the products and services of the industry’s leading IT security solution providers. Learn more at www.kaspersky.co.uk. For the latest on antivirus, anti-spyware, anti-spam and other IT security issues and trends, visit http://www.securelist.com.
