Kaspersky researchers have discovered a new Trojan spy called SparkKitty which targets smartphones on iOS and Android. It sends images from an infected phone and information about the device to the attackers. This malware was embedded in apps related to crypto and gambling, as well as in a trojanized TikTok app, and was distributed on App Store and Google Play, as well as on scam websites. Experts suggest that the goal of the attackers is to steal cryptocurrency assets from residents of Southeast Asia and China. Users in UK are also potentially at risk of facing a similar cyber threat.
Kaspersky has notified Google and Apple about the malicious apps. Certain technical details suggest that the new malware campaign is linked to the previously discovered SparkCatTrojan — malware (the first of its kind on iOS) with a built-in optical character recognition (OCR) module that allows it to scan image galleries and steal screenshots containing cryptocurrency wallet recovery phrases or passwords. The SparkKitty case is the second time in a year that Kaspersky researchers have found a Trojan stealer on App Store, following SparkCat.
iOS
On App Store, the Trojan pretended to be an app related to cryptocurrencies
— 币coin. On phishing pages mimicking the official iPhone App Store, the
malware was distributed under the guise of TikTok and gambling applications.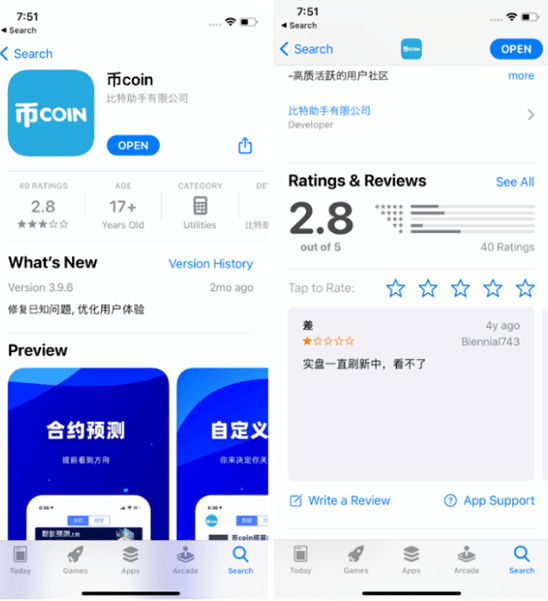
"One of the vectors for
the Trojan's distribution turned out to be fake websites where the attackers
tried to infect the victims' iPhones. iOS has several legitimate ways to
install programs not from the App Store. In this malicious campaign, the
attackers used one of them — special developer tools for distributing corporate
business applications. In the infected version of TikTok, during authorization,
the malware, in addition to stealing photos from the smartphone gallery,
embedded links to a suspicious store in the person's profile window. This store
only accepts cryptocurrencies, which increases our concerns about it,” explains
Sergey Puzan, a malware expert at Kaspersky.
Android
The attackers targeted users both on third-party
websites and on Google Play, passing off the malware as various crypto
services. For example, one of the infected applications — a messenger called
SOEX with a cryptocurrency exchange function — was downloaded from the official
store over 10,000 times. 
Experts also found APK files of infected apps (these can be installed directly on Android smartphones bypassing official stores) on third-party websites that are likely related to the detected malicious campaign. They are positioned as investment crypto projects. The websites on which these applications were posted were advertised on social networks, including YouTube.
"After the apps were installed, they functioned as promised in their description. But at the same time, photos from the smartphone gallery were sent to the attackers. The attackers may later try to find various confidential data in the images, for instance, crypto wallet recovery phrases to access the victims' assets. There are indirect signs that the attackers are interested in people's digital assets: many of the infected apps were related to crypto, and the trojanized TikTok app also had a built-in store that accepted payment for goods only in crypto," comments Dmitry Kalinin, a malware expert at Kaspersky.
A detailed report about this attack is available on Securelist.com.
To avoid becoming a victim of this malware, Kaspersky recommends the following safety measures:
- If you have installed one of the infected applications, remove it from your device and do not use it until an update has been released to eliminate the malicious functionality.
- Avoid storing screenshots containing sensitive information in your gallery, including cryptocurrency wallet recovery phrases. Passwords, for example, could be stored in specialized applications such as Kaspersky Password Manager.
- Reliable cybersecurity software, like Kaspersky Premium, can prevent malware infections. Due to the architectural features of the Apple operating system, the Kaspersky solution for iOS shows the user a warning if it detects an attempt to transfer data to the attacker's command server, and blocks the attacker from transferring data.
- If an app asks for permission to access the phone's photo library, consider if this app really needs it.
About Kaspersky Threat
Research
The Threat Research team is a leading authority
in protecting against cyberthreats. By actively engaging in both threat
analysis and technology creation, our TR experts ensure that Kaspersky’s
cybersecurity solutions are deeply informed and exceptionally potent, providing
critical threat intelligence and robust security to our clients and the broader
community.
