Network Threat Protection
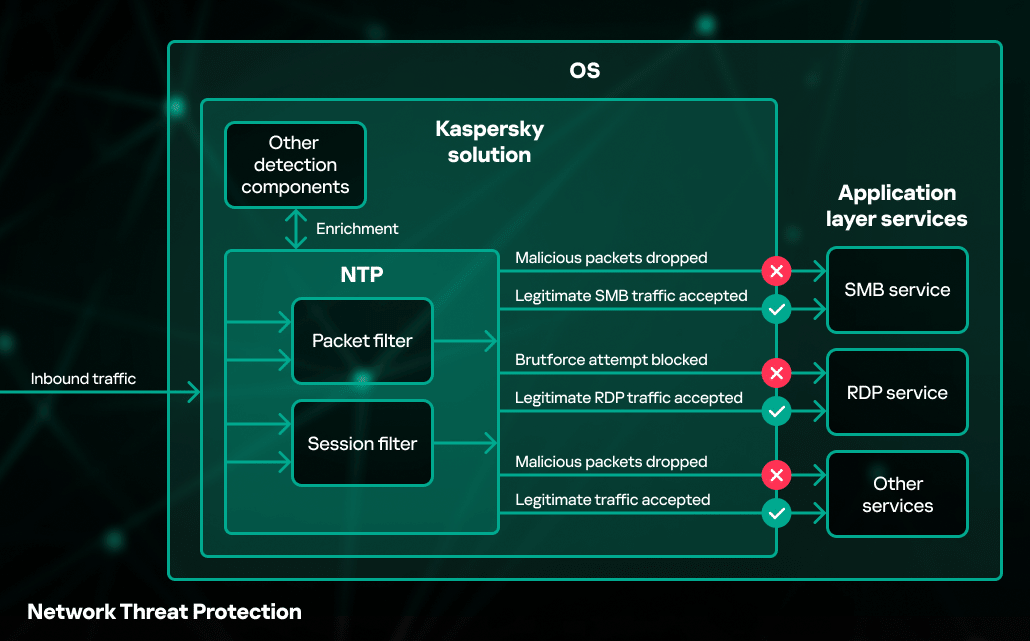
Network Threat Protection (NTP) is a component of Kaspersky products that detects and blocks network-based attacks. Such attacks include exploits against network vulnerabilities in software applications, system services and even operating systems, as well as port scanning, flood attacks and password brute-force attempts. Attackers can use a variety of techniques that can be detected on the network layer:
- known exploits against vulnerabilities in critical network services to perform intrusion attempts. One of the most famous examples is the EternalBlue exploit for the Windows operating system which uses a bug in the SMB protocol parser to corrupt kernel memory and execute remote code on the victim's machine;
- different port scanning techniques to determine services that are running on the victim's machine, and retrieve useful information, such as a list of open directories, SMB shares, OS and service versions, etc.;
- password brute-force techniques to determine login credentials for network services (RDP, FTP, SSH, etc.), to be used down the line for exfiltration of sensitive information;
- flood attacks to prevent or slow down other users from accessing network services of the attacked host. The aim is to exhaust capabilities of the network services on the attacked host to serve large amounts of traffic, or connections to it.
These types of threats are successfully covered by NTP to protect endpoints from being compromised. This technology acts as a network packet filter and operates before actual traffic processing by services or software applications. Once it detects a malicious packet, it drops the network session and may also block network connections from the remote host. NTP is deeply integrated into other components and detection technologies, so the Threat Behavior Engine can grab detection information from the NTP component.


