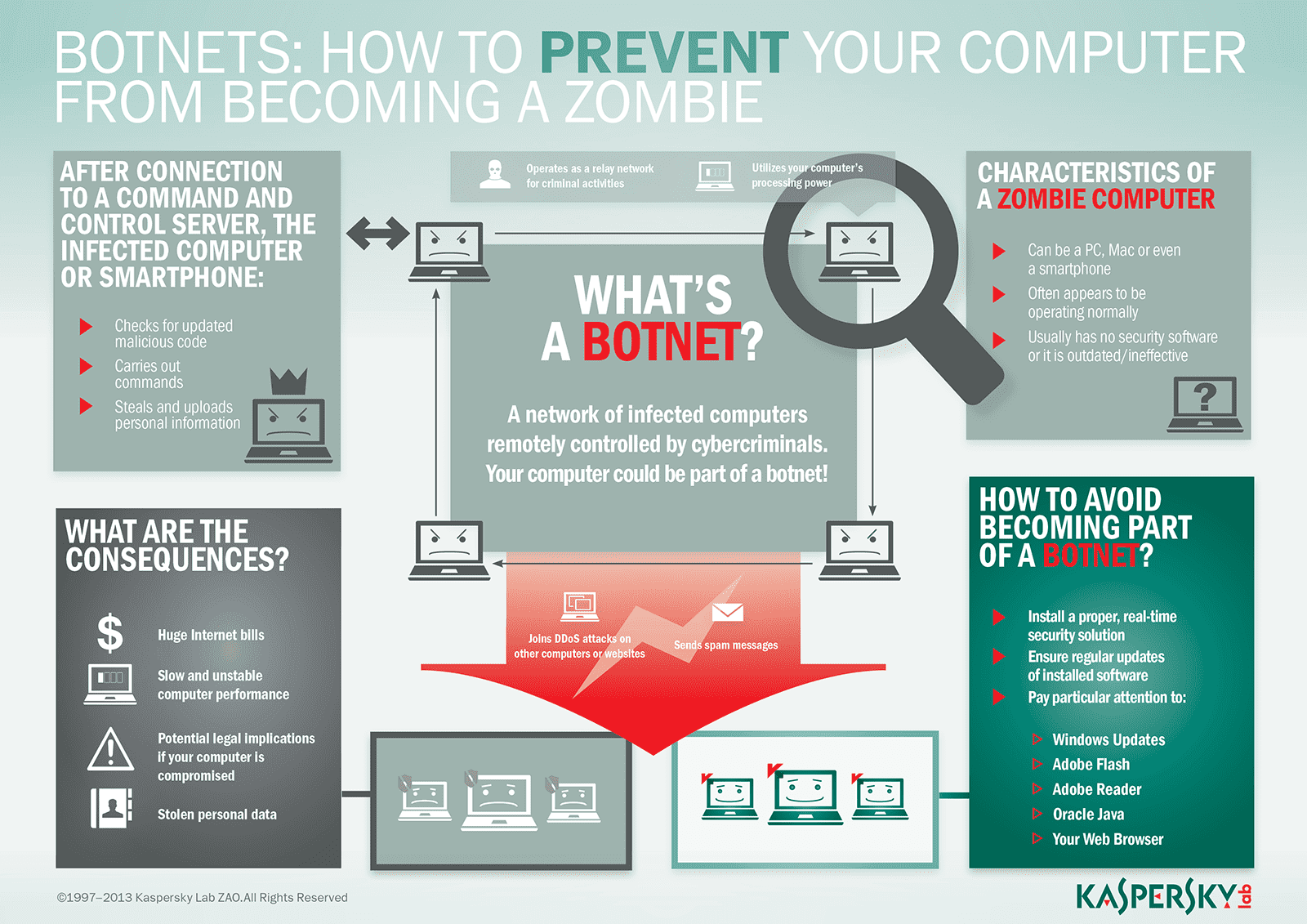
Botnet Definition
Botnets are networks of hijacked computer devices used to carry out various scams and cyberattacks. The term “botnet” is formed from the word’s “robot” and “network.” Assembly of a botnet is usually the infiltration stage of a multi-layer scheme. The bots serve as a tool to automate mass attacks, such as data theft, server crashing, and malware distribution.
Botnets use your devices to scam other people or cause disruptions — all without your consent. You might ask, “what is a botnet attack and how does it work?” To expand this botnet definition, we’ll help you understand how botnets are made and how they are used.
How Botnet Works
Botnets are built to grow, automate, and speed up a hacker’s ability to carry out larger attacks.
One person or even a small team of hackers can only carry out so many actions on their local devices. But, at little cost and a bit of time invested, they can acquire tons of additional machines to leverage for more efficient operations.
A bot herder leads a collective of hijacked devices with remote commands. Once they’ve compiled the bots, a herder uses command programming to drive their next actions. The party taking command duties may have set up the botnet or be operating it as a rental.
Zombie computers, or bots, refer to each malware-infected user device that’s been taken over for use in the botnet. These devices operate mindlessly under commands designed by the bot herder.
Basic stages of building a botnet can be simplified into a few steps:
- Prep and Expose — hacker exploits a vulnerability to expose users to malware.
- Infect — user devices are infected with malware that can take control of their device.
- Activate — hackers mobilize infected devices to carry out attacks.
Stage 1 exposure starts with hackers finding a vulnerability in a website, application, or human behavior. The goal is to set the user up for being unknowingly exposed to a malware infection. You’ll commonly see hackers exploit security issues in software or websites or deliver the malware through emails and other online messages.
In stage 2, the user gets infected with the botnet malware upon taking an action that compromises their device. Many of these methods either involve users being persuaded via social engineering to download a special Trojan virus. Other attackers may be more aggressive by using a drive-by download upon visiting an infected site. Regardless of the delivery method, cybercriminals ultimately breach the security of several users’ computers.
Once the hacker is ready, stage 3 initiates by taking control of each computer. The attacker organizes all of the infected machines into a network of “bots” that they can remotely manage. Often, the cybercriminal will seek to infect and control thousands, tens of thousands, or even millions of computers. The cybercriminal can then act as the boss of a large “zombie network” — i.e. a fully assembled and active botnet.
You’re probably still are asking, “what does a botnet do?” Once infected, a zombie computer allows access to admin-level operations, such as:
- Reading and writing system data
- Gathering the user’s personal data
- Sending files and other data
- Monitoring the user’s activities
- Searching for vulnerabilities in other devices
- Installing and running any applications
What is Botnet Controllable?
Candidates for botnet recruitment can be any device that can access an internet connection.
Many devices we use today have some form of computer within them — even ones you might not consider. Nearly any computer-based internet device is vulnerable to a botnet meaning the threat is growing constantly. To protect yourself, take note of some common devices that are hijacked into botnets:
Traditional computers like desktops and laptops that run on Windows OS or macOS have long been popular targets for botnet construction.
Mobile devices have become another target as more people continue to use them. Smartphones and tablets have notably been included in botnet attacks of the past.
Internet infrastructure hardware used to enable, and support internet connections may also be co-opted into botnets. Network routers and web servers are known to be targets.
Internet of Things (IoT) devices include any connected devices that share data between each other via the internet. Alongside computers and mobile devices, examples might include:
- Smart home devices (thermometers, security cameras, televisions, speakers, etc.)
- In-vehicle infotainment (IVI)
- Wearable devices (smartwatches, fitness trackers, etc.)
Collectively, all these devices can be corrupted to create massive botnets. The technology market has become oversaturated with low-cost, low-security devices, leaving you particularly vulnerable as a user. Without anti-virus malware, bot herders can infect your devices unnoticed.
How Do Hackers Control a Botnet?
Issuing commands is a vital part of controlling a botnet. However, anonymity is just as important to the attacker. As such, botnets are operated via remote programming.
Command-and-control (C&C) is the server source of all botnet instruction and leadership. This is the bot herder's main server, and each of the zombie computers gets commands from it.
Each botnet can be led by commands either directly or indirectly in the following models:
- Centralized client-server models
- Decentralized peer-to-peer (P2P) models
Centralized models are driven by one bot herder server. A variation on this model may insert additional servers tasked as sub-herders, or “proxies.” However, all commands trickle down from the bot herder in both centralized and proxy-based hierarchies. Either structure leaves the bot herder open to being discovered, which makes these dated methods less than ideal.
Decentralized models embed the instruction responsibilities across all the zombie computers. As long as the bot herder can contact any one of the zombie computers, they can spread the commands to the others. The peer-to-peer structure further obscures the identity of the bot herder party. With clear advantages over older centralized models, P2P is more common today.
What Are Botnets Used For?
Botnet creators always have something to gain, whether for money or personal satisfaction.
- Financial theft — by extorting or directly stealing money
- Information theft — for access to sensitive or confidential accounts
- Sabotage of services — by taking services and websites offline, etc.
- Cryptocurrency scams — using users’ processing power to mine for cryptocurrency
- Selling access to other criminals — to permit further scams on unsuspecting users
Most of the motives for building a botnet are similar to those of other cybercrimes. In many cases, these attackers either want to steal something valuable or cause trouble for others.
In some cases, cybercriminals will establish and sell access to a large network of zombie machines. The buyers are usually other cybercriminals that pay either on a rental basis or as an outright sale. For example, spammers may rent or buy a network to operate a large-scale spam campaign.
Despite the many potential benefits for a hacker, some people create botnets just because they can. Regardless of motive, botnets end up being used for all types of attacks both on the botnet-controlled users and other people.
Types of Botnet Attacks
While botnets can be an attack in themselves, they are an ideal tool to execute secondary scams and cybercrimes on a massive scale. Common botnet schemes include some of the following:
Distributed Denial-of-Service (DDoS) is an attack based on overloading a server with web traffic to crash it. Zombie computers are tasked with swarming websites and other online services, resulting in them being taken down for some time.
Phishing schemes imitate trusted people and organizations for tricking them out of their valuable information. Typically, this involves a large-scale spam campaign meant to steal user account information like banking logins or email credentials.
Brute force attacks run programs designed to breach web accounts by force. Dictionary attacks and credential stuffing are used to exploit weak user passwords and access their data.
How to Protect Yourself from Botnets
Considering the threats to the safety of yourself and others, it is imperative that you protect yourself from botnet malware.
Fortunately, software protections and small changes to your computer habits can help.
6 Tips for protecting yourself against Botnets
- Improve all user passwords for smart devices. Using complex and long passwords will help your devices stay safer than weak and short passwords. Such as ‘pass12345.
- Avoid buying devices with weak security. While this isn’t always easy to spot, many cheap smart home gadgets tend to prioritize user convenience over security. Research reviews on a product’s safety and security features before buying.
- Update admin settings and passwords across all your devices. You’ll want to check all possible privacy and security options on anything that connects device-to-device or to the internet. Even smart refrigerators and Bluetooth-equipped vehicles have default manufacturer passwords to access their software systems. Without updates to custom login credentials and private connectivity, hackers can breach and infect each of your connected devices.
- Be wary of any email attachments. The best approach is to completely avoid downloading attachments. When you need to download an attachment, carefully investigate, and verify the sender’s email address. Also, consider using antivirus software that proactively scans attachments for malware before you download.
- Never click links in any message you receive. Texts, emails, and social media messages can all be reliable vehicles for botnet malware. Manually entering the link into the address bar will help you avoid DNS cache poisoning and drive-by downloads. Also, take an extra step to search for an official version of the link.
- Install effective anti-virus software. A strong internet security suite will help to protect your computer against Trojans and other threats. Be sure to get a product that covers all your devices, including Android phones and tablets.
Botnets are difficult to stop once they’ve taken root in user’s devices. To reduce phishing attacks and other issues, be sure you guard each of your devices against this malicious hijack.
Related articles:

